Cybersecurity and Data Privacy


Supporting the SDGs Goals
Goal 11:
Goal and Performance Highlights
Long-Term Goal
Goal
Performance
Goal
Performance
Goal
Performance
Challenges and Opportunities
Ratch Pathana Group has established policies to ensure the security of the organization's information, enabling it to prevent, manage, and mitigate risks from cyber threats. This also ensures that Ratch Pathana Energy appropriately manages cybersecurity risks.
Furthermore, these policies aim to prevent cybercrime, attacks, sabotage, espionage, and various errors, while also complying with the Royal Gazette announcements regarding the Cybersecurity Act B.E. 2562 (2019) and the Personal Data Protection Act B.E. 2562 (2019).
This is done with consideration for the three fundamental elements of information security:
Confidentiality
Integrity
Availability
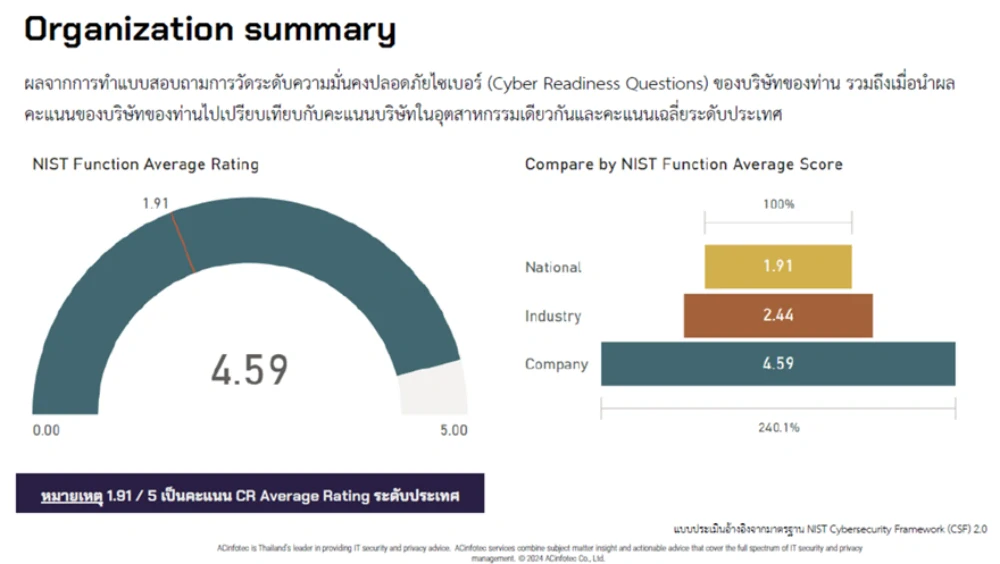
And Ratch Pathana Energy has adopted the NIST Cybersecurity Framework to enhance its security foundation, which comprises 5 key functions:
Management Approach and Value Creation
The company recognizes and prioritizes the continuous and effective enhancement of operational security. This involves establishing measures to prevent issues arising from various threats associated with undesirable use of information technology systems, which could cause overall damage to the company. To prevent legal violations and ensure compliance with relevant regulations, the company has established the Information Technology Security Policy and the Personal Data Protection Policy as follows:
Information Technology Security Policy
The Company prioritizes Information Technology security and utilizes the NIST Cybersecurity Framework in conjunction with the frameworks of the Cybersecurity Act and the Personal Data Protection Act. This is to prevent potential damage from cyber threats and to ensure operations comply with relevant laws and regulations. The key policies and measures are as follows:
-
System and Data Access Control
- We limit access rights to information systems to align with users' duties and responsibilities.
- Authentication is enforced before every system usage.
- Network areas are segmented, and access to critical systems is restricted.
-
System and Device Management
- We control access to computer equipment and network systems.
- Unauthorized use is prevented, and data security is strictly managed.
- Security devices such as Firewall, Antivirus, NDR, PAM, and DLP are installed.
-
Data Backup and Emergency Plan
- Data backup system and a disaster recovery plan are in place to ensure continuous service in emergencies, following the 3-2-1 standard.
-
Risk Monitoring and Assessment
- Information security risks are regularly monitored and assessed at least once a year.
-
Policy and Practice Updates
- Policies are reviewed and updated at least once a year to remain current with system changes and evolving threats.
- A committee for the Cybersecurity Act and the Personal Data Protection Act has been established for oversight.
-
Accountability for Damages
- Responsibilities are defined for the IT Section Manager and system administrators in cases of damages resulting from policy violations or breaches.
Personal Data Protection Policy
The Company and its subsidiaries prioritize the protection of personal data, recognizing it as a fundamental right to privacy that must be safeguarded in accordance with the Constitution of the Kingdom of Thailand and the Universal Declaration of Human Rights. The Company supports the protection of human rights in line with the principles of the UN Global Compact, as well as compliance with the Personal Data Protection Act B.E. 2562 (2019) and related laws. This ensures the highest level of personal data protection, guided by the following key policies and measures:
-
Scope of Data Usage
- We collect, use, and disclose personal data only when necessary and in alignment with specified purposes, requiring the data owner's consent
-
Personal Data Protection Measures
- We strictly define data access and processing rights.
- Data transfers to foreign countries must adhere to security measures that are equivalent to or higher than our own.
- We immediately notify data owners in cases of breaches or data leaks, along with a damage remediation plan.
-
Data Owner Rights
- Data owners have the right to access, rectify, delete, or withdraw consent for the processing of their personal data. This also includes the right to object to and restrict data processing.
-
Penalties and Responsibilities
- Employees who violate this policy will face disciplinary action and may be prosecuted under the law.
- The company is not responsible for damages resulting from actions by the data owner or individuals authorized by the data owner.
-
Data Retention Period
- We retain personal data only for as long as necessary for the stated purposes and as required by law.
Cybersecurity and Personal Data Usage Training
In 2024, the company organized cybersecurity and personal data usage training for employees. This was conducted in collaboration with the National Cyber Security Agency (NCSA), featuring a session on "Cybersecurity Awareness (IT Awareness)" held on October 9, 2024, at Ratchaphatthana Energy PCL. Online training was also provided for subsidiary companies. 93% of employees participated in the training.


Cybersecurity and Personal Data Protection Performance in 2024
| Title | Frequency |
|---|---|
| Cyberattack on the company | 0 |
| Personal Data Breach | 0 |